Intro - Maltego, is an open source intelligence and forensics application. This is a GUI tool so looks different. Maltego is an information gathering tool that allows you to visually see relationships.
Maltego allows you to enumerate network and domain information like:
· Domain Names
· Whois Information
· DNS Names
· Netblocks
· IP Addresses etc
Maltego also allows you to enumerate People information like:
· Email addresses associated with a person’s name
· Web sites associated with a person’s name
· Phone numbers associated with a person’s name
· Social groups that are associated with a person’s name
· Companies and organizations associated with a person’s name etc
Maltego also allows you to:
· Do simple verification of email addresses
· Search blogs for tags and phrases
· Identify incoming links for websites
· Extract metadata from files from target domains
This tool has really lots of feature I will try to explain more and more with examples but my dear readers I want to advice all of you try all features of this tool and if you are facing any kind of problem while experimenting on this tool you can ask your question here through your valuable comments
1. How to open Maltego
A. GUI Method
Application → Kali Linux → Information gathering → DNS Analysis → Maltego
(click image for large view)
B. open terminal type maltego and hit enter
2. Because We are using first time maltego so we need to log in. Follow the image for info
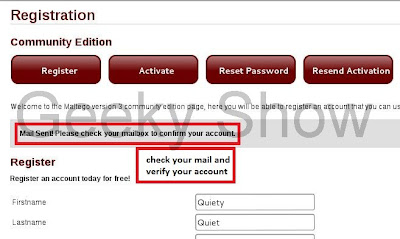
3. We are new user so we need to register before using this tool. Follow the image.
4. Fill up all details for completing the registration. Follow the image.
5. After completing your registration go to your mail Id and verify your account by clicking on verification link which is send y maltego.
6. After verifying your maltego account login with your registered email id and password.
7. Soon you will see a welcome massage.
8. Just click on Next
9. Click on Finish
10. Click on cancel we will do it manually.
11. Click on new icon (see image) for gathering the information
12. by clicking left button of mouse drag the domain in Main view
13. Double click on domain icon and rename it into your target domain. Here I am taking mcdonalds.com as example.
14. Here we are searching for top level domain for our target domain. First right click on domain then
Run Transform → All Transforms → To Domain ( Find other TLDs)
15. Here we got the result of TLD search.
16. Now we are to gain more information about these domains. First of all select all domains by dragging left mouse button or you can select one by one press Shift + left click
17. After selecting all domains, right click one of them and then
Run Transform → All Transforms → To Website (Quick Lookup)
Here we are going to search all website which are associate with these domains
18. Here is the result sorry this image is not clear because I want to show you full result page.
19. Well here we are just replacing the a website icon I have targeted www.mcdonalds.com for more info follow the image. This is not a necessary part but you should learn it.
20. Here we are going to find the IP address of our target website. Right click on target website then
Run Transform → Resolve to IP → To IP Address (DNS)
21. Here we got the IP address of our target website
22. Here I am explaining you many things so don’t be confuse its just graphical view changes.
You can change you view as you can see on image there are some option like Main View, Bubble View, Entity list try all by yourself for visiting how interesting it is. And another side if you will zoom out then you can see your information in a better identical view more info on image.
23. Here we are going to Find Email Id of our target website which is www.mcdonalds.com
Right click on target website and then
Run Transform → All Transforms → Mirror: Email address found
24. You can see on the image we have got email ids.
25. Here we are running all transforms just for showing you how many information you can gather with this tool. I am doing this because I can’t show you every option like domain search, person info, phone number, NS server etc. You have to do experiment with it and it takes time. So enjoy
Right click on Domain then
Run Transform → All Transforms → All Transforms
26. Click on Yes
27. Read all T & C. I know no one going to read it :D. after reading check the box and click on Run.
28. Here is the Result. As you can see each of info has a separate color to indicate it so just enjoy it.
(click image for large view)





 Translate
Translate






























![[Image: image1_zps1ba326d9.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image1_zps1ba326d9.jpg)
![[Image: image2_zpsffcf021f.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image2_zpsffcf021f.jpg)
![[Image: image3_zps85f6aa32.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image3_zps85f6aa32.jpg)
![[Image: image4_zps29fa4d64.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image4_zps29fa4d64.jpg)
![[Image: image5_zpsf83a99b1.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image5_zpsf83a99b1.jpg)
![[Image: image6_zps002b2bf8.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image6_zps002b2bf8.jpg)
![[Image: image7_zpsfb061ca9.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image7_zpsfb061ca9.jpg)
![[Image: image8_zpsc0a432ae.jpg]](http://i790.photobucket.com/albums/yy187/cyb3rl0g1c/image8_zpsc0a432ae.jpg)
